
Call Us
1300 786 040
Plan, Do, Check, Act to Achieve:
Cyber Resilience & Compliance

Establish
Roadmap & Scope

Implement
Security Controls
Measure and Assess
Performance & Effectiveness
Remediate gaps and drive
Continuous Improvement

We are Experts in
Security Compliance
At Cintelis, we help businesses navigate the complex landscape of cyber security compliance requirements, ensuring robust protection against threats and full compliance with industry standards.

Thorough Risk Assessments
Identify and evaluate potential security risks to ensure your organisation remains resilient against emerging threats and compliant with regulatory standards.

Continuous Compliance Monitoring
Regularly track and assess your compliance status with automated tools, ensuring ongoing adherence to regulations like ISO 27001, SOC 2, NIST CSF, APRA CPS 234, and the ACSC Essential 8.
How to automate
ISO 27001 and SOC 2 compliance
How Security Compliance
Our Services

ISO 27001
Internal Audit
We assess and verify compliance with the requirements from Annex A deemed applicable in ISMS Statement of Applicability

Risk Assessment
Workflow Automation
We identify and address vulnerabilities in real-time, ensuring efficient and accurate risk management.
IRAP Protected
Readiness Assessment
Verify and capture the implementation of controls from the Information Security Manual (ISM) by a Cloud Service Provider (CSP)

Monitor
Third-Party Vendors
We implement monitoring and assessment of third-party vendors to ensure compliance with security standards and mitigate risks

Automate
Compliance Tracking
We setup automated tools and dashboards for tracking and reporting of compliance status against regulatory requirements.

Verify and Validate
Cloud Security
Conduct assessment of SaaS, PaaS, IaaS configuration to ensure alignment with SOC 2 controls, PCI-DSS, NIST CSF, CIS, APRA CPS 234 and other regulatory requirements.

Governance of
Indentity & Access Management
Design and implementation of passwordless authentication, FIDO security keys, biometric authentication, and NFC access cards to comply with local regulations.

Comprehensive
Digital Forensic Analysis
Collect and analyse digital evidence, trace malicious activities, including blockchain transactions, and provide in-depth reports to support your legal and compliance requirements..
Enhance Cyber Resilience
Why Compliance Assessment?
Compliance assessments ensure your organisation adheres to industry standards and regulatory requirements. They help identify gaps in your security controls, optimize risk management, and ensure robust protection against cyber threats.
- Risk Assessments
- Internal Audits
- External Audits
- Security architecture validation
- Automated Compliance Tracking
- Continuous Vendor Monitoring
- Data Mapping and Inventory

Get Updates
Blog Posts and News Feeds

Understanding Retrieval Augmented Generation (RAG) Systems
As the AI landscape evolves, the need for more accurate and efficient search methodologies has emerged. One such approach gaining prominence is Retrieval Augmented Generation

Governance, Quality Control, and Ethical Oversight in AI
In today’s fast-paced digital landscape, AI Governance is crucial for ensuring that AI systems are ethical, secure, and trustworthy. As Artificial Intelligence (AI) continues to

MLOps Made Easy with JFrog
Machine learning (ML) is rapidly becoming a cornerstone of modern software development, with Gartner predicting that by 2027, over 90% of new business software applications

Attack Path Modeling: A Deep Dive
In today’s digital age, cybersecurity is more crucial than ever. With threats lurking around every corner, how can organizations stay one step ahead? Enter Darktrace’s

Types of Software Security Vulnerabilities
Most software security vulnerabilities fall into one of the following categories: Buffer overflow – This vulnerability occurs when data is written beyond the limits of
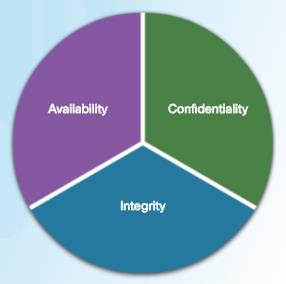
Confidentiality, Integrity, and Availability
Confidentiality, integrity and availability, known as the CIA triad, is a guideline for information security for an organization. Confidentiality ensures the privacy of data by
FAQs
ISO 27001 Compliance Planning
Developing a roadmap for your ISMS implementation and ISO 27001 certification begins with creating a detailed plan. The initial step is to purchase the ISO 27001 standard and the ISO 27002 guide for implementing ISO 27001. Organize your implementation project by incorporating the following tasks: implementing a Plan-Do-Check-Act (PDCA) process to identify challenges and gaps for remediation, considering the costs of ISO 27001 certification relative to your organization’s size and number of employees, utilizing project planning tools such as project management software, Gantt charts, or Kanban boards, and defining the scope of work from planning to completion.
The scope will depend on factors such as the size of your organization, the type of data you handle, and the methods you use to process or interact with that data. To establish the scope of your ISMS, follow these steps: decide which business areas will be covered by your ISMS and which ones will be out of scope, consider additional security controls for processes that need to pass ISMS-protected information across the trust boundary, and communicate the scope of your ISMS to stakeholders.
This team may include internal employees like engineers and compliance specialists, external contractors, or a combination of both, depending on your needs. Follow these steps for this phase: select engineers and technical staff with experience in information security to construct and implement the necessary security controls for ISO 27001, build a governance team with management oversight, and incorporate key members of top management (senior leadership and executive management) to assign responsibility for strategy and resource allocation.
Before your team begins working, it’s crucial to ensure everyone has a clear understanding of the assets the ISMS will be protecting. Conduct an inventory of information assets, which may include, all assets where information is stored, processed, and accessible, including record information assets like data and personnel, physical assets like laptops, servers, and physical building locations, and intangible assets like intellectual property, brand, and reputation. Assign each asset a classification and an owner to ensure they are appropriately inventoried, classified, protected, and handled. Finally, meet with your team to discuss this inventory and ensure everyone is aligned.
Perform a risk assessment by following these steps to identify and analyze the risks facing your organization:
- Establish and document a risk management framework to ensure consistency.
- Identify scenarios in which information, systems, or services could be compromised.
- Determine the likelihood or frequency with which these scenarios could occur.
- Evaluate the potential impact of each scenario on the confidentiality, integrity, or availability of your data, systems, and services.
- Rank risk scenarios based on overall risk to the organization’s objectives.
Develop a risk register by turning your detailed risk assessment findings into a practical record. With your ISO 27001 certification team, check off these items to create a viable risk register:
- Record and manage your organisation’s risks identified during the risk assessment.
- Summarise each identified risk.
- Indicate the impact and likelihood of each risk.
- Rank risk scenarios based on overall risk to the organisation’s objectives.
Documenting a risk treatment plan is the next step to address and mitigate the risks you’ve identified. Follow these steps to start taking action: design a response for each risk, known as a risk treatment, assign an owner to each identified risk and each risk mitigation activity, establish target timelines for the completion of risk treatment activities, and implement your risk mitigation treatment plan while tracking the progress of each task.
Completing the Statement of Applicability is a crucial step in the ISO 27001:2022 compliance process. Annex A of the ISO 27001:2022 standard lists the security controls and practices that should be considered for compliance. These controls are selected based on identified risks or your organization’s specific requirements, and some may be excluded if they are not relevant to your environment. To complete the Statement of Applicability, follow these steps: review the 93 controls listed in Annex A, select the controls relevant to the risks identified in your risk assessment, and complete the Statement of Applicability by listing all Annex A controls, justifying the inclusion or exclusion of each control in your ISMS implementation.
After completing the Statement of Applicability and your initial risk assessment, you should have a clear understanding of how to proceed with your ISO 27001 compliance. Follow these steps to address each of the controls included in your Statement of Applicability: assign owners to each of the security controls to be implemented, determine a method to track the progress and goals for each control, and build a framework for establishing, implementing, maintaining, and continually improving the ISMS. Include information or references to supporting documentation regarding:
- Information security objectives
- Leadership and commitment
- Roles, responsibilities, and authorities
- Approach to assessing and treating risk
- Control of documented information
- Communication
- Internal audit
- Management review
- Corrective action and continual improvement
- Policy violations
- All of the Annex A controls that you have selected
Establishing employee training is crucial, as any employee could unknowingly give hackers access to your data. A core part of ISO 27001 compliance involves training employees to prevent fraud and data theft. Follow these steps to train your employees on data security and establish a plan for ongoing training: define expectations for personnel regarding their role in ISMS maintenance, train personnel on common threats facing your organization and how to respond, establish disciplinary or sanction policies for personnel found out of compliance with information security requirements, make security training part of the onboarding process for new employees, and conduct regular training to ensure awareness of new policies and procedures.
Conducting regular management reviews is essential to maintain your ISO 27001 compliance, as various factors can unintentionally disrupt your compliance, such as updates to your network, tool failures, or lapses in following policies. Follow these steps to maintain your ISO 27001 compliance: plan reviews at least once per year, and consider a quarterly review cycle if your organization is large or if your infrastructure changes frequently, ensure the ISMS and its objectives remain effective, verify that senior management stays informed, and ensure that risks or deficiencies can be promptly addressed.
The list of mandatory ISO 27001:2022 documentation includes:
- Scope of the ISMS (Clause 4.3): ISMS Scope document
- Information security policy (Clause 5.2): Information Security Policy
- Risk assessment and risk treatment process (Clause 6.1.2): Risk Assessment and Treatment Methodology
- Statement of Applicability (Clause 6.1.3 d): Statement of Applicability
- Risk treatment plan (Clauses 6.1.3 e, 6.2, and 8.3): Risk Treatment Plan
- Information security objectives (Clause 6.2): List of Security Objectives
- Risk assessment and treatment report (Clauses 8.2 and 8.3): Risk Assessment & Treatment Report
- Inventory of assets (Control A.5.9): Inventory of Assets, or List of Assets in the Risk Register
- Acceptable use of assets (Control A.5.10): IT Security Policy
- Incident response procedure (Control A.5.26): Incident Management Procedure
- Statutory, regulatory, and contractual requirements (Control A.5.31): List of Legal, Regulatory, and Contractual Requirements
- Security operating procedures for IT management (Control A.5.37): Security Procedures for IT Department
- Definition of security roles and responsibilities (Controls A.6.2 and A.6.6):Agreements, NDAs, and specifying responsibilities in each security policy and procedure
- Definition of security configurations (Control A.8.9): Security Procedures for IT Department
- Secure system engineering principles (Control A.8.27): Secure Development Policy
The list of non-mandatory ISO 27001:2022 documentation includes:
- Procedure for Document and Record Control (clause 7.5, control A.5.33)
- Procedure for Internal Audit (clause 9.2)
- Procedure for Corrective Action (clause 10.2)
- Information Classification Policy (controls A.5.10, A.5.12, and A.5.13)
- Information Transfer Policy (control A.5.14)
- Access Control Policy (control A.5.15)
- Password Policy (controls A.5.16, A.5.17, and A.8.5)
- Supplier Security Policy (controls A.5.19, A.5.21, A.5.22, and A.5.23)
- Disaster Recovery Plan (controls A.5.29, A.5.30, and A.8.14)
- Mobile Device, Teleworking, and Work from Home Policy (controls A.6.7, A.7.8, A.7.9, and A.8.1)
- Procedures for Working in Secure Areas (controls A.7.4 and A.7.6)
- Clear Desk and Clear Screen Policy (control A.7.7)
- Bring Your Own Device (BYOD) Policy (controls A.7.8 and A.8.1)
- Disposal and Destruction Policy (controls A.7.10, A.7.14, and A.8.10)
- Backup Policy (control A.8.13)
- Encryption Policy (control A.8.24)
- Change Management Policy (control A.8.32)
ISO 27001 records that are mandatory:
- Trainings, skills, experience, and qualifications (Clause 7.2): Training certificates and CVs
- Monitoring and measurement results (Clause 9.1): Measurement Report
- Internal audit program (Clause 9.2): Internal Audit Program
- Results of internal audits (Clause 9.2): Internal Audit Report
- Results of the management review (Clause 9.3): Management Review Minutes
- Results of corrective actions (Clause 10.2): Corrective Action Form
- Logs of user activities, exceptions, and security events (Control A.8.15): Automatic logs in information systems
- A.5.7 Threat intelligence–>Incident Management Procedure
- A.5.23 Information security for use of cloud services–>Supplier Security Policy
- A.5.30 ICT readiness for business continuity–>Disaster Recovery Plan
- A.7.4 Physical security monitoring–>Procedures for Working in Secure Areas
- A.8.9 Configuration management–>Security Procedures for IT Department
- A.8.10 Information deletion–>Disposal and Destruction Policy
- A.8.11 Data masking–>Secure Development Policy
- A.8.12 Data leakage prevention–>Security Procedures for IT Department
- A.8.16 Monitoring activities–>Security Procedures for IT Department
- A.8.23 Web filtering–>Security Procedures for IT Department
- A.8.28 Secure coding–>Secure Development Policy
Performing an ISO 27001 internal audit is essential to ensure you’ll pass your official audit. Conduct an internal audit to address all areas of non-compliance by completing these tasks:
- Examine each of the requirements from Annex A that you deemed applicable in your ISMS Statement of Applicability and verify that they are in place.
- Assign in-house employees who were not involved in ISMS development and maintenance to conduct the internal audit, or hire an independent third party.
- Share internal audit results, including nonconformities, with the ISMS team and senior management.
- Address any issues identified in your internal audit before proceeding with the external audit.
- Verify compliance with the applicable requirements from Annex A in your ISMS Statement of Applicability.
Undergoing an external audit of your ISMS to obtain ISO 27001 certification is the final step. Follow these steps for your external audit:
- Select an independent ISO 27001 auditor.
- Complete the Stage 1 Audit, which consists of an extensive documentation review; obtain the auditor’s feedback regarding your readiness to move to the Stage 2 Audit.
- Complete the Stage 2 Audit, which consists of tests performed on the ISMS to ensure proper design, implementation, and ongoing functionality; evaluate the fairness, suitability, and effective implementation and operation of controls.
Addressing any nonconformities identified during your ISO 27001 audit is crucial. If issues arise, follow these steps:
- Ensure that all requirements of the ISO 27001 standard are addressed.
- Verify that your organization is following the processes it has specified and documented.
- Confirm that your organization is upholding contractual requirements with third parties.
- Address specific nonconformities identified by the ISO 27001 auditor.
- Receive the auditor’s formal validation following the resolution of nonconformities.
If your auditor does not find any nonconformities, you can skip this step.
Planning for subsequent ISO 27001 audits and surveillance audits is essential to maintain your certification. Keep these timelines in mind:
- Prepare to perform surveillance audits every year of your certification cycle.
- Perform a full ISO 27001 audit once every three years.
To ensure you’re always ISO 27001 compliant, use a compliance automation platform that helps your organization stay secure. A compliance automation platform provides ongoing monitoring to notify you anytime your organization falls out of compliance. Vanta’s trust management platform offers guidance with step-by-step instructions for identifying gaps and implementing ISO 27001 controls, automating up to 80% of the work required to obtain ISO 27001 certification. See how you can automate your ISO 27001 implementation by requesting a demo from Vanta.
Testimonials
What our clients think
Read below the testimonials of our happy customers

Brenton Avery
Oakpont, CEO

Yanek Hebting
Greatcell Solar Materials, CEO

Jay Haybatov
DekkoSecure, Founder
Get in touch
50% of Businesses Get Breached Each Year
Don’t be the next: we can help you!











